We are revolutionizing your approach to Digital Defense
Say goodbye to unmanaged services and unnecessary licenses. Choose your stack and unlock the power of managed cybersecurity services.

ThreatCTRL
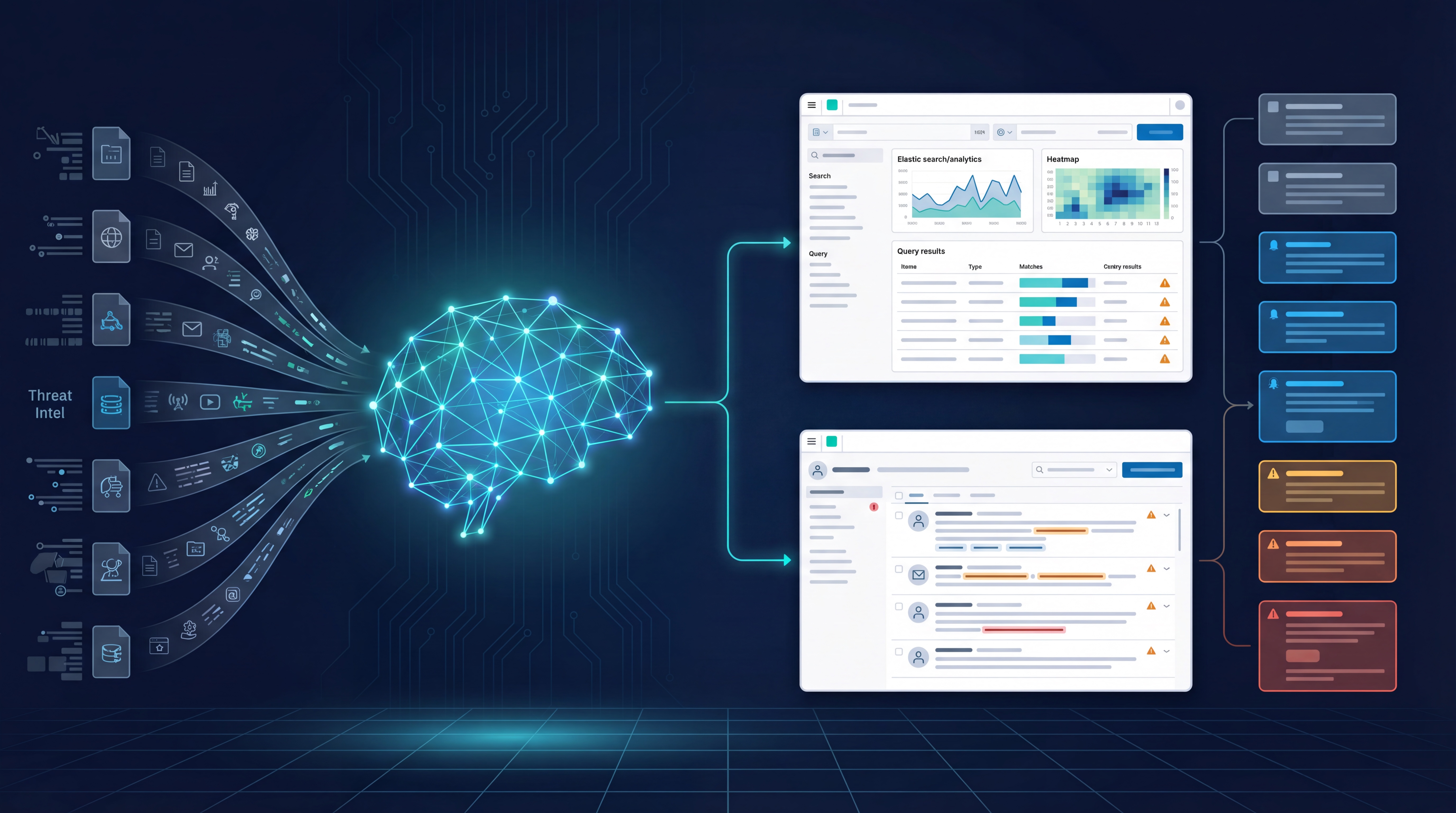
This solution streamlines security management by providing complete visibility and control over an organization's security posture, enabling swift decision-making and enhanced security responsiveness. With ThreatCTRL, organizations gain the insight needed to safeguard their environments effectively and efficiently.

Autonomous EDR
Autonomous XDR offers swift and effective safeguarding by simplifying cybersecurity through advanced automation and integration. It sets new security standards by providing automated, rapid responses to threats, ensuring robust defense against various cyber challenges. Autonomous XDR streamlines cybersecurity, delivering fast and efficient protection through automation and integration.

SIEM
The main use case for this SIEM solution is to detect, analyze, and respond to cybersecurity threats and incidents, ensuring timely intervention and mitigation. By leveraging superior technology and seamless integration, Sofecta Labs' SIEM Solution empowers organizations with the tools needed for effective threat detection, providing a secure and resilient digital infrastructure.
Discover Sofecta Labs' SIEM Solution, leveraging Elastic Security for unmatched visibility into security events and enhancing swift response with XDR integration. This solution excels in detecting, analyzing, and responding to cyber threats, providing detailed reports for all captured data. It's designed to fortify your cybersecurity posture with effective threat detection and timely mitigation, ensuring a secure digital environment.

SOAR Automation
Key benefits include significantly enhanced operational efficiency through the automation of repetitive tasks, enabling security teams to concentrate on strategic analysis. Moreover, it centralizes security alerts to improve visibility and decision-making, while also ensuring scalable and standardized incident responses across the organization.
Sofecta Labs' SOAR Automation Solution elevates your security operations by providing streamlined efficiency, enhanced visibility, and consistent response strategies. Safeguard your organization against cyber threats with our state-of-the-art automation solution.

Threat Hunting
We dive deeply into customer data—network traffic, endpoint details, and logs—to detect anomalies and suspicious behaviors that signal advanced or novel threats. Our method transcends conventional signature-based detection by incorporating behavioral analysis, which is crucial for identifying sophisticated threats that evade standard detection frameworks.
The core of our Threat Hunting strategy is to actively search for signs of compromise based on intelligence about current attack patterns, ensuring we can uncover and neutralize threats before they escalate. This vigilant, intelligence-driven approach guarantees enhanced security by pinpointing and mitigating risks missed by traditional security defenses.

Identity Protection
After the configuration, we'll establish monitoring for user behavior and access patterns, analyzing activities to detect anomalies, suspicious actions, or unusual activities that could signal a compromised account or unauthorized access. With IDM integration to SOAR, we can provide automated, rapid response actions in case of threats.

Mobile Threat Defense
Key features include comprehensive network, system, and application threat protection, from phishing attempts and OS vulnerabilities to 0-day malware. The service also offers automated threat response and remediation, with easy-to-configure policies, user guidance for manual remediation, and more.
By seamlessly integrating with SIEM and SOAR platforms, Sofecta Labs enables rapid detection and efficient remediation of mobile threats, ensuring your devices are safeguarded against the latest vulnerabilities and attacks.

Email Security
Sofecta Labs offers an advanced Email Security solution that shields an organization from diverse email threats such as malware, ransomware, business email compromise, QR code phishing, credential phishing, and VIP impersonation. The technology reduces an organization's attack surface, operationalizes threat intelligence, and automates user reporting of suspicious emails to foster a herd immunity against repeated threats.
This comprehensive solution stands as a robust defense against email-delivered attacks, excelling in essential cybersecurity use cases like inbound email security, attack surface reduction, advanced pattern matching through YARA Rule Analysis, purple and red teaming, new domain blocking and threat hunting.
With Sofecta Labs' Email Security solution, organizations gain a comprehensive shield that equips them with faster detection, detailed investigation, and decisive action to ensure the integrity and security of company communications.

Vunerability Management
By integrating directly with SIEM and SOAR platforms, our solution not only identifies vulnerabilities but also facilitates rapid detection and swift remediation. Our solution transforms vulnerability data into a strategic asset, enhancing your security posture and resilience against cyber threats. With Sofecta Labs, secure your network and stay one step ahead in your defenses against cyber threats.

Cloud Security
Our service, integrated with SIEM and SOAR platforms, offers rapid vulnerability detection, facilitates swift remediation, and helps effectively manage cloud security risks. This ultimately improves your security posture and aids in ensuring compliance with various security standards and regulations.
Choose the best defense for your business
Holistic
Integrated
Experience seamless connectivity to our solution stack

Sublime Security is a programmable, AI-powered, cloud email security platform for Microsoft 365 and Google Workspace environments. It is used to block email attacks such as phishing, BEC, malware, threat hunt, and auto-triage user reports.
The Sublime Security integration collects data for Audit, Email Message(MDM Schema) and Message Event logs using REST API and AWS-S3 or AWS-SQS

This integration sniffs network packets on a host and dissects known protocols.
Monitoring your network traffic is critical to gaining observability and securing your environment — ensuring high levels of performance and security. The Network Packet Capture integration captures the network traffic between your application servers, decodes common application layer protocols and records the interesting fields for each transaction.

This Active Directory Entity Analytics integration allows users to securely stream User Entities data to Elastic Security via the Active Directory LDAP look-ups. When integrated with Elastic Security, this valuable data can be leveraged within Elastic for risk-scoring scenarios (e.g., context enrichments) and detecting advanced analytics (UBA) use cases.

The Living off the Land Attack (LotL) Detection package contains a supervised machine learning model, called ProblemChild and associated assets, which are used to detect living off the land (LotL) activity in your environment.

The Lateral movement detection model package contains assets that detect lateral movement based on file transfer activity and Windows RDP events. This package requires a Platinum subscription. Please ensure that you have a Trial, Platinum, or Enterprise subscription before proceeding.

Collect logs from Amazon Security Lake with Elastic Agent. This Amazon Security Lake integration helps you analyze security data, so you can get a more complete understanding of your security posture across the entire organization.

The AWS WAF integration allows you to monitor AWS Web Application Firewall (WAF), a web application firewall for protecting against common web exploits.

The AWS Security Hub integration collects and parses data from AWS Security Hub REST APIs.

The Amazon GuardDuty integration collects and parses data from Amazon GuardDuty Findings REST APIs.

The Microsoft 365 Defender integration allows you to monitor Alert, Incident (Microsoft Graph Security API) and Event (Streaming API) Logs. Microsoft 365 Defender is a unified pre and post-breach enterprise defense suite that natively coordinates detection, prevention, investigation, and response across endpoints, identities, email, and applications to provide integrated protection against sophisticated attacks.

The CrowdStrike Falcon integration allows you to easily connect your CrowdStrike Falcon platform to Elastic for seamless onboarding of alerts and telemetry from CrowdStrike Falcon and Falcon Data Replicator. Elastic Security can leverage this data for security analytics including correlation, visualization and incident response.

Cisco Meraki offers a centralized cloud management platform for all Meraki devices such as MX Security Appliances, MR Access Points and so on. Its out-of-band cloud architecture creates secure, scalable and easy-to-deploy networks that can be managed from anywhere. This can be done from almost any device using web-based Meraki Dashboard and Meraki Mobile App. Each Meraki network generates its own events.






.svg)




















.png)
.png)