From Insight to Action: Accelerating Threat Hunting with AI Agents - How Sofecta Labs combines automated intelligence with agentic AI to hunt threats before they strike

In cybersecurity, time is the only currency that matters. The gap between a new threat being discovered and an attacker exploiting it is shrinking rapidly. For business leaders, the challenge is no longer just knowing about a threat—it is determining, in minutes rather than days, if that threat exists within their own environment.
At Sofecta Labs, we have long recognized that traditional, manual threat hunting cannot keep pace with modern adversaries. That is why we have evolved our approach. We are moving beyond simple automation into the era of Agentic AI—autonomous workflows that don’t just read the news, but actively hunt for danger across your infrastructure.
The Foundation: Automated Intelligence Gathering
To understand where we are going, it is important to understand where the data comes from. Effective defense starts with knowing what the enemy is doing.
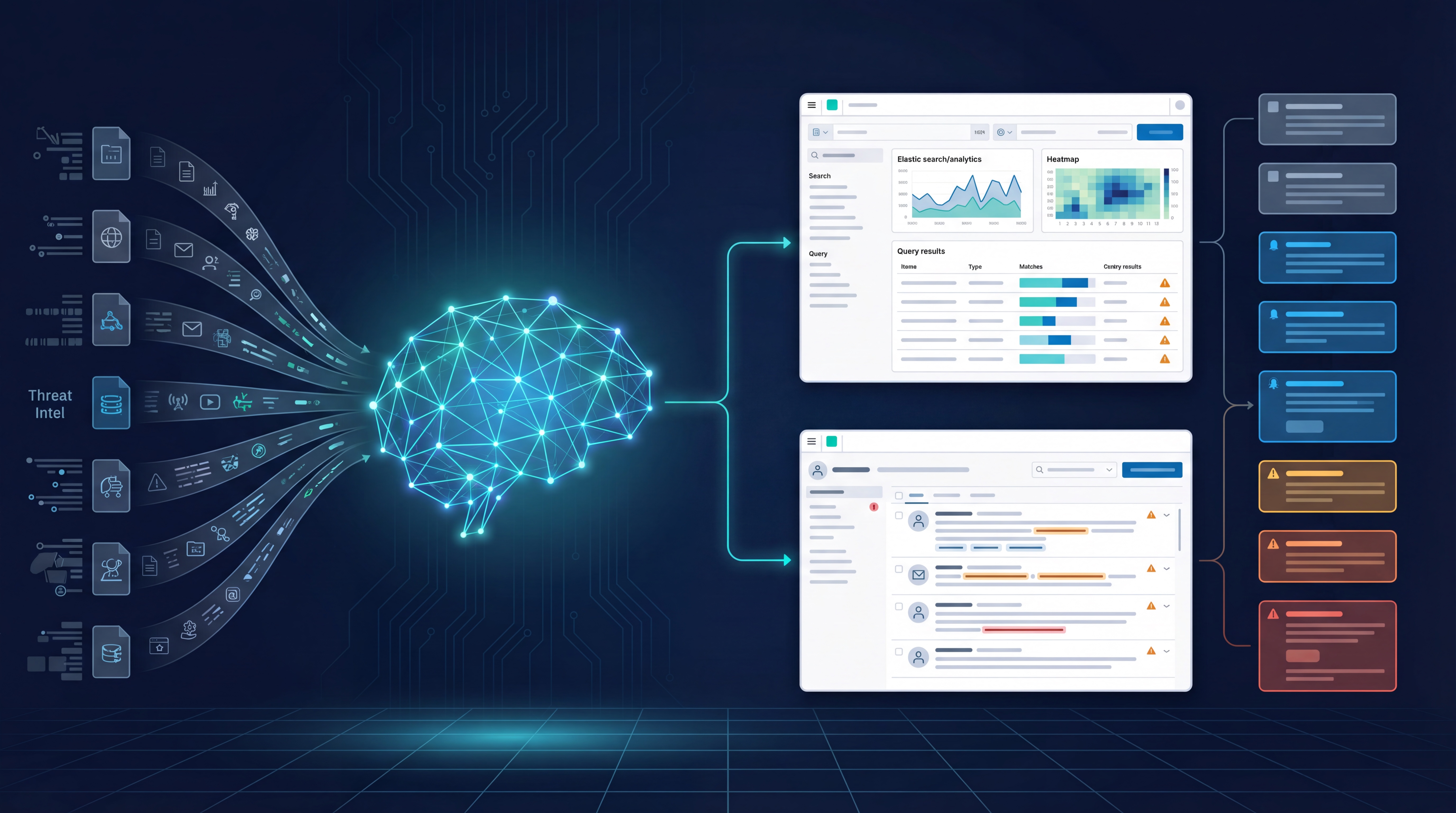
Every single day, our systems automatically ingest cybersecurity intelligence from nearly 30 distinct sources, including vendor advisories, research papers, and underground forums. But raw data is noise, not intelligence.
Our AI engine classifies, summarizes, and analyzes this influx of information. It immediately extracts references to vulnerable software and services, cross-referencing them against our clients’ specific software inventories. If a client is running a version of software that has just been compromised globally, our analysts are notified instantly.
This was our baseline. But we asked ourselves: Why stop at notification? Why not start the hunt immediately?
The Evolution: AI Agents in the Driver’s Seat
Identifying a vulnerability is critical, but detecting active exploitation is where the battle is won or lost. Recently, we extended our capabilities by deploying AI Agentic Flows.
Think of these agents not as passive chatbots, but as digital members of our security team that work alongside our human analysts. Here is how this advanced workflow operates:
1. Intelligent Assessment When new threat intelligence arrives, our AI analyzes the content to determine if it is “huntable.” It asks: Does this threat have technical indicators we can search for?
2. Autonomous Hunting If the threat is actionable, the AI Agent takes charge. It doesn’t wait for a human to write a query. Instead, it cooperates directly with our security stack:
- Deep Dive with Elastic: The agent generates and executes custom ESQL (Elasticsearch Query Language) queries to scour customer environments for suspicious logs or network activity.
- Endpoint & Email Analysis with Sublime: Simultaneously, the agent interfaces with Sublime Security, running custom MQL (Message Query Language) queries to detect malicious email patterns or endpoint behaviors.
3. Pre-Validated Case Creation The AI aggregates its findings into a cohesive “Threat Hunt Case.” It doesn’t just dump data; it provides a summary of what it looked for, what it found, and why it matters.
4. Human Decision Making This is where the synergy of man and machine shines. Our seasoned analysts receive a flagged, pre-validated case. They don’t spend hours gathering data; they review the AI’s findings to decide whether to escalate the hunt or close the case.
The Business Impact: The “Protection Edge”
For our clients, this technological leap translates into tangible business advantages:
- Drastic Reduction in Dwell Time: We are no longer waiting for a scheduled review to look for new threats. The moment intel is published globally, our agents are hunting it locally.
- Focus on High-Value Security: By offloading the repetitive work of data querying to AI agents, our human experts focus entirely on complex decision-making and strategic defense.
- Scalable Vigilance: Whether it is 3:00 PM or 3:00 AM, the AI agents ensure that your organization’s defense posture is always active and reactive to the latest global trends.
Conclusion
At Sofecta Labs, we believe that technology alone cannot secure an organization, but technology guided by expertise is unstoppable. By integrating AI agents into our platform, we are saving tremendous amounts of time and eliminating the “noise” that plagues modern security operations.
We are not just watching the threat landscape; we are actively patrolling it. This allows our clients to operate with confidence, knowing they possess a protection edge that keeps them ahead of the curve—and ahead of the attackers.



.png)